GNSS provides precise positioning, navigation and timing functions, and plays a key role in military and national economy industries, and its safety has become the focus of people's attention.GNSS signal strength is weak and civil GNSS has an open structure, so it is easy to be interfered or spoofed. This paper mainly analyzes the GNSS spoofing detection and mitigation techniques.
- Background
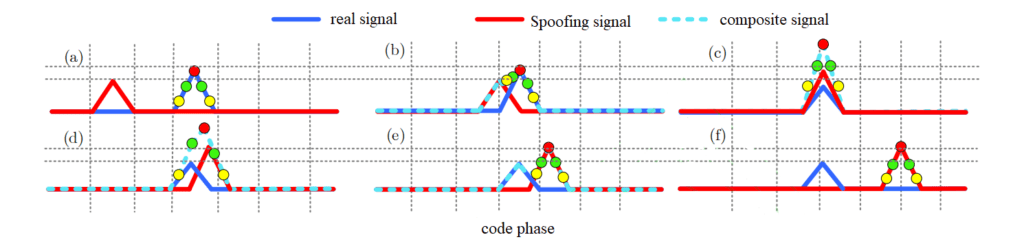
The application of GNSS in military and civilian fields is gradually widespread, and the dependence of society on the PNT (Positioning Navigation and Timing) service provided by GNSS is rapidly increasing, at this time, the security and stability of GNSS has also received great attention. As shown in Figure 1, the real signal is launched from the satellite and is maliciously attacked in the process of reaching the receiver. Due to the weak strength of the navigation signal, the open signal modulation method, and the predictability of some navigation data, GNSS is extremely susceptible to spoofed interference, which is fatal to the navigation system. The so-called spoofing jamming is that all kinds of transmitters transmit the same or similar signals with GNSS signals, so that receivers mistakenly think that they are real signals transmitted by satellites, and capture and track them, thus making receivers produce wrong position and time information.
Navigation jamming has gradually changed from suppression jamming, which prevents the reception of navigation signals, to spoofing jamming, which invades the navigation system and tampers with navigation information. Compared with suppression jamming, spoofing jamming is not easy to be detected and is more harmful. According to the analysis of the influence of spoofing signal on the GNSS vector tracking loop, the spoofing signal affects the tracking loop of the target receiver, destroys the consistency of the tracking signal, causes the loop to be unlocked and gradually controls the target receiver. The realization process of spoofing is as follows:
(a): deception preparation. Prior to the attack, the spoofing device probes the antenna of the target receiver to assess its position and speed, and estimates the satellite signals from the antenna of the target receiver. The spoofed signal in this phase has the same frequency as the real signal, lower power, and a phase difference of two code slices;
(b): the code rate of the spoofed signal is rapidly adjusted, gradually approaching the real signal, and the power is gradually increased, but still lower than the real signal power;
(c): the signals are synchronized. The power of the spoofed signal is increasing and the code phase is aligned with the real signal;
(d): power and code rate continue to increase, and the tracking loop continues to lock onto the spoofed signal at this point.
(e): signal transmission. The spoofed signal uses a higher power level to remove the tracking loop between the real signal and the target receiver, enabling tracking of the spoofed signal;
(f): the spoofing device takes full control of the target receiver.
Fig. 2 shows the realization of the spoofing process:
2. GNSS spoofing interference detection
2.1 Combined navigation-based spoofing interference detection method
Inertial navigation, visual navigation and other navigation modes are not affected by spoofing interference, combining GNSS with other navigation modes, spoofing interference detection is carried out through the difference of navigation results of different navigation modes. If the difference exceeds a set threshold, it is judged to be under spoofing attack.
The combination of inertial navigation and GNSS can achieve the purpose of spoofing detection by consistency checking of features such as trajectory, acceleration and position. The deception interference detection method based on combined navigation is more effective for forwarding deception interference detection. The signal of the forwarding deception interference lags behind the real signal, which leads to the time of the deceived device earlier than the real time or the position of the deception device deviates from the real position, and the deception interference detection can be realized through the combination navigation. For generative jamming, the detection performance of this method is related to the deflection speed of the spoofing signal. If the deception signal is induced too fast and the change per unit time exceeds the error range of other navigation methods, it will be detected successfully. Meanwhile, the increase of the positioning accuracy of other navigation methods will improve the detection ability of the method.
Overall, the detection performance of the deception interference detection method based on combined navigation is better than that based on a single antenna receiver, but the method requires additional hardware and the system composition is more complicated.
2.2 Machine Learning Based Deceptive Interference Detection Methods
Deceptive interference detection can be regarded as a binary classification problem, machine learning has a wide range of applications and better performance in binary classification problems, and many scholars use machine learning to improve the performance of existing deception detection methods. The application of machine learning can realize the fusion of multiple feature parameters for detection, and some research papers have used the signal's carrier-to-noise ratio, pseudo-distance, carrier frequency and other information as feature parameters to detect spoofing interference at the same time, which improves the success rate of the detection while increasing the robustness of the detection method, and better copes with different spoofing interferences.
Compared with the traditional spoofing interference detection algorithm, the detection method applying machine learning has a higher detection success rate, and the main research direction of this detection algorithm is to choose a model with better detection effect, smaller computation amount and more effective model input variables. However, the success rate of detection is affected by the dataset used for training and validation, and applying the method to real scenarios may not achieve the detection rate described in the literature. Therefore, when conducting research on machine learning-based spoofed interference detection methods, it is recommended to use standard datasets, which can be referred to the TEXBAT dataset provided by the Radionavigation Laboratory at the University of Texas at Austin and the GPS and Galileo spoofed dataset OAKBAT provided by Oak Ridge National Laboratory.
2.3 Spoofing Interference Detection Methods Based on Single-Antenna Receiver Signal Characteristics
At the beginning of the research on spoofing detection methods, scholars carried out spoofing detection by looking for the signal characteristics of single antenna receivers that changed after being spoofed. Since the spoofed signal cannot perfectly simulate the power of the real signal, the addition of spoofed interference will cause changes in signal power, noise power, carrier-to-noise ratio, etc. In the capture tracking phase, the spoofed signal under the covert spoofing strategy needs to enter the tracking loop and slowly increase the power and change the phase, and this process causes misalignment between the phases of the real code and the spoofed code and the appearance of multiple correlation peaks.
After the spoofed signal enters the tracking loop, if the spoofed signal of covert spoofing changes too fast or the spoofing strategy is overt spoofing, it will cause sudden changes in the information of pseudo-distance, time, speed measurement result and positioning result. Based on the above detection characteristics, the deception interference detection methods based on single antenna receiver signal characteristics are categorized as shown in Table 1.
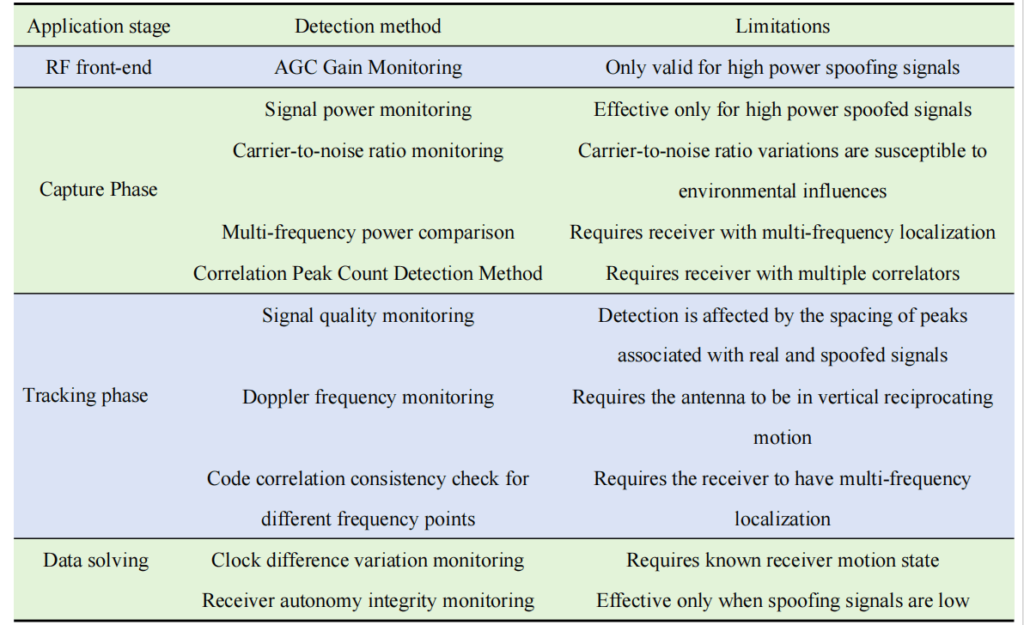
Based on the single antenna receiver signal characteristics of spoofing interference detection method has the characteristics of low cost, flexibility and high efficiency, is currently the most researched and most widely used method, the combination of this method with other detection methods, to improve the detection probability of a variety of spoofing interference is the main direction of future research.
3. Spoofed Interference Suppression
GNSS spoofed interference suppression refers to the process of mitigating the effects of spoofed interference and restoring positioning accuracy of the receiver under spoofed attack, which is carried out after the spoofed signal detection is completed or at the same time with the detection. Compared with spoofed interference detection, there are fewer studies on spoofed interference suppression methods, and this paper combed the existing spoofed interference suppression methods based on the existing literature.
3.1 Signal Reconstruction
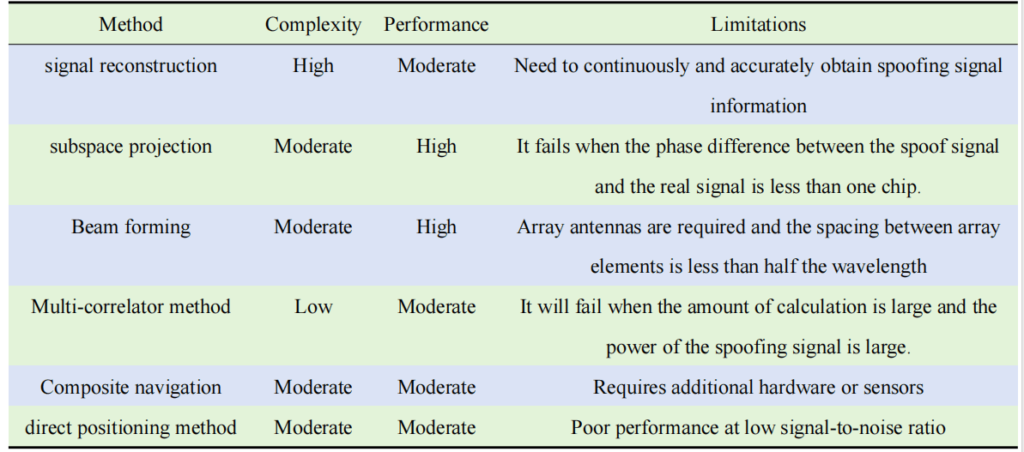
Signal reconstruction method refers to obtaining the code delay, Doppler frequency, carrier phase and signal amplitude of the spoofed interference after completing the spoofed interference detection to reconstruct the spoofed signals, and then subtracting the reconstructed spoofed signals from the original IF navigation signals to get the navigation signals without spoofed signals and realize the spoofed interference suppression. The deception signal classification module can classify the tracked signals into deception signals and real signals, and reconstruct and eliminate the signals based on the information of the deception signals, and then re-detect the processed signals, and if there are deception signals, reconstruct and eliminate the deception signals again.
The spoofed signal is reconstructed by estimating the amplitude and phase of the spoofed signal, the reconstructed signal is canceled with the delayed original signal, and the performance is evaluated by defining the interference cancellation ratio (ICR). From the above research simulation results, it is found that the signal reconstruction method has good suppression effect, but the method needs to continuously and accurately obtain the information of the spoofed signal, which is very complex and difficult to realize.
3.2 Subspace projection
It is difficult and arithmetic to accurately estimate all the parameters of the spoofed signal, which limits the application of the signal reconstruction method. A research proposes a subspace projection method, which estimates the carrier frequency and code phase of the spoofed signal by capturing and tracking, constructs the signal subspace of the spoofed signal based on the quasi-orthogonality of its PRN code, and orthogonally projects the received signal onto the subspace to suppress the spoofed signal, so as to realize the capture and tracking of the real signal. The carrier frequency of the spoofed signal is estimated by the parameter estimation method, which has lower arithmetic complexity.
Compared with the signal reconstruction method, this method reduces the required spoofed signal information and has better robustness. However, if the phase difference between the spoofed signal and the real signal is less than one code slice, the suppression function will be lost, which indicates that the method is unable to detect spoofed signals with smaller deviations.
3.3 Beam Formation
Adaptive beam forming can control the radiation direction map of the array antenna to suppress the spoofing signal in the direction of the spoofing interference source and enhance the real navigation signal in the direction of the navigation satellite. Beam forming technology and array antenna-based spoofing interference detection technology are used at the same time, firstly, the array antenna acquires the baseband signal and establishes the loop matrix, realizes the detection of spoofing interference according to the eigenvalue test, and then realizes the suppression of spoofing interference and the enhancement of the real signals through the beam forming technology.
Adaptive beamforming has many applications in suppressed interference suppression, and the algorithm is relatively mature, which can be directly applied to spoofed interference suppression, and can simultaneously realize suppressed and spoofed interference suppression. However, with the increase of interference direction, the array antenna needs to further increase the number of antenna elements, so the complexity and high cost of the equipment is the main reason to limit its wide application.
3.4 Multi-correlator method
Introducing the multi-correlator structure in the receiver can capture and track the real signal and spoofing at the same time, and then confirm the real signal and exclude the spoofing signal through the judgment method to realize the detection and suppression of spoofing signal. When multiple signals are present in the received signal, multi-signal tracking is performed using the multi-correlator without any a priori knowledge of the spoofed signal. The baseband signal is processed using the multi-path estimating delay lockloop (MEDLL) technique to obtain the amplitude, propagation delay and carrier phase of the signal, denoted as
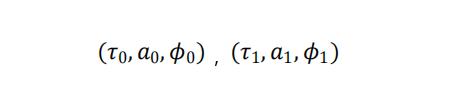
Then, based on the estimated values of amplitude, propagation delay and carrier phase of the signals, one set of signals is removed from the original baseband signals and tracked separately to obtain the tracking results of the other set of signals.
Table 2 summarizes and analyzes the different spoofed interference suppression methods.
4. Conclusion and Prospect
Based on the research results at home and abroad, by comparing the performance of different defense methods and combining the development trend of current research, the focus in future research can be on the following five aspects:
- Multiple detection methods fusion detection.
- Defense technology based on array antenna.
- Combining traditional defense methods with machine learning.
- Strengthening the research of spoofing interference suppression.
- Establishment of improved standard datasets.
Additionally, numerous GNSS hardware units now incorporate features for interference detection and spoofing detection. For instance, the ER-GNSS-M03 integrates internal technologies like Jam Shield adaptive anti-jamming and U-Auto Align multipath suppression. Even in challenging environments, it maintains commendable performance. Similarly, the ER-SR-680 boasts robust anti-jamming capabilities and exceptional stability, making it suitable for unattended base stations. Widely employed in scientific research fields such as surveying and mapping, meteorology, seismic monitoring, displacement tracking, and high-precision positioning, it stands as a versatile tool for various applications.
I will appreciate it if you find this article help you a lot, for more information, please read the following articles and products.
More Technical Questions
1. Construction Surveying: Unleashing New Energy with the Help of GNSS
2. Performance Analysis of GNSS RTK Timing
3. Intelligent Urban Positioning: Using Multi-GNSS with 3D Mapping
4. Positioning Performance Comparison of GNSS PPP
5. Precision Mapping in Mining Operations: The Role of GNSS Augmentation Technology
6. Application of GNSS-RTK Positioning Technology in ICV Testing
Products in Article