In this article, we will explore five proven methods to enhance GNSS security, mitigating the risks associated with malicious attacks and ensuring the continued functionality of GNSS systems.
- Background
Imagine driving your car in the city center, checking the navigator's screen, only to discover that it indicates you are outside the city, near the airport. This scenario exemplifies the use of Global Navigation Satellite System (GNSS) spoofing technology, where GNSS coordinates are replaced by a stronger fake signal broadcasted from the ground, drowning out authentic satellite signals.
There are many practical applications for this focusd from car theft (there are known cases of theft of Transport International Routiers (TIRs) to interfering with the navigation of yachts and tankers. Therefore, protective systems against this type of attack began to appear. Such hacking is called “false GNSS-like signals” or “GNSS spoofing” (Fig. 1).
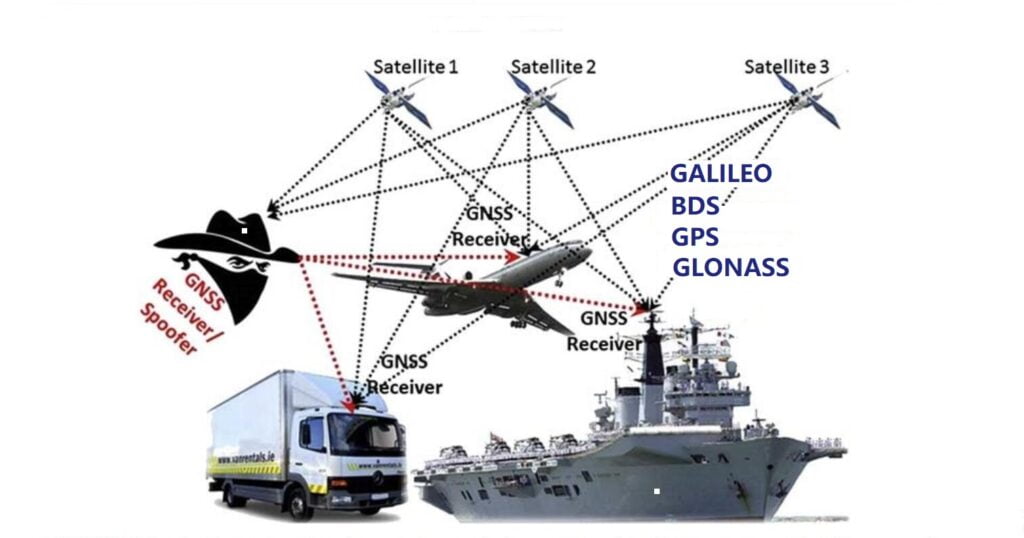
The development of satellite navigation technology and electronic information technology has promoted the wide application of navigation, positioning, and timing technology and also made it face a series of threats and challenges, including intentional spoofing. Spoofing directly leads to “wrong” location information of the positioning terminal and “wrong” time information of the timing terminal, thus affecting the normal production and life order.
There is no doubt that the frequency of jamming or/and spoofing will increase, as methods are constantly being improved.
The GNSS is, in general, a reliable system, and in order to keep it that way, professional GNSS receivers must be protected from all possible vulnerabilities, both accidental and man-made. GNSS spoofing may become quite dangerous for military and also for civil use of GNSS. Unlike military GNSS signals, civilian GNSS satellite signals are not encrypted or verified. This allows even relatively uninspired adversaries to easily jam, alter, or fake them.
- Types of GNSS Vulnerabilities
Spoofing of GNSS signals is a set of techniques that a malicious user intentionally uses in order to induce false ranging measurements to a legitimate user. As GNSS further penetrates into the civil infrastructure, it becomes a tempting target that could be exploited by individuals, groups, or hostile countries.
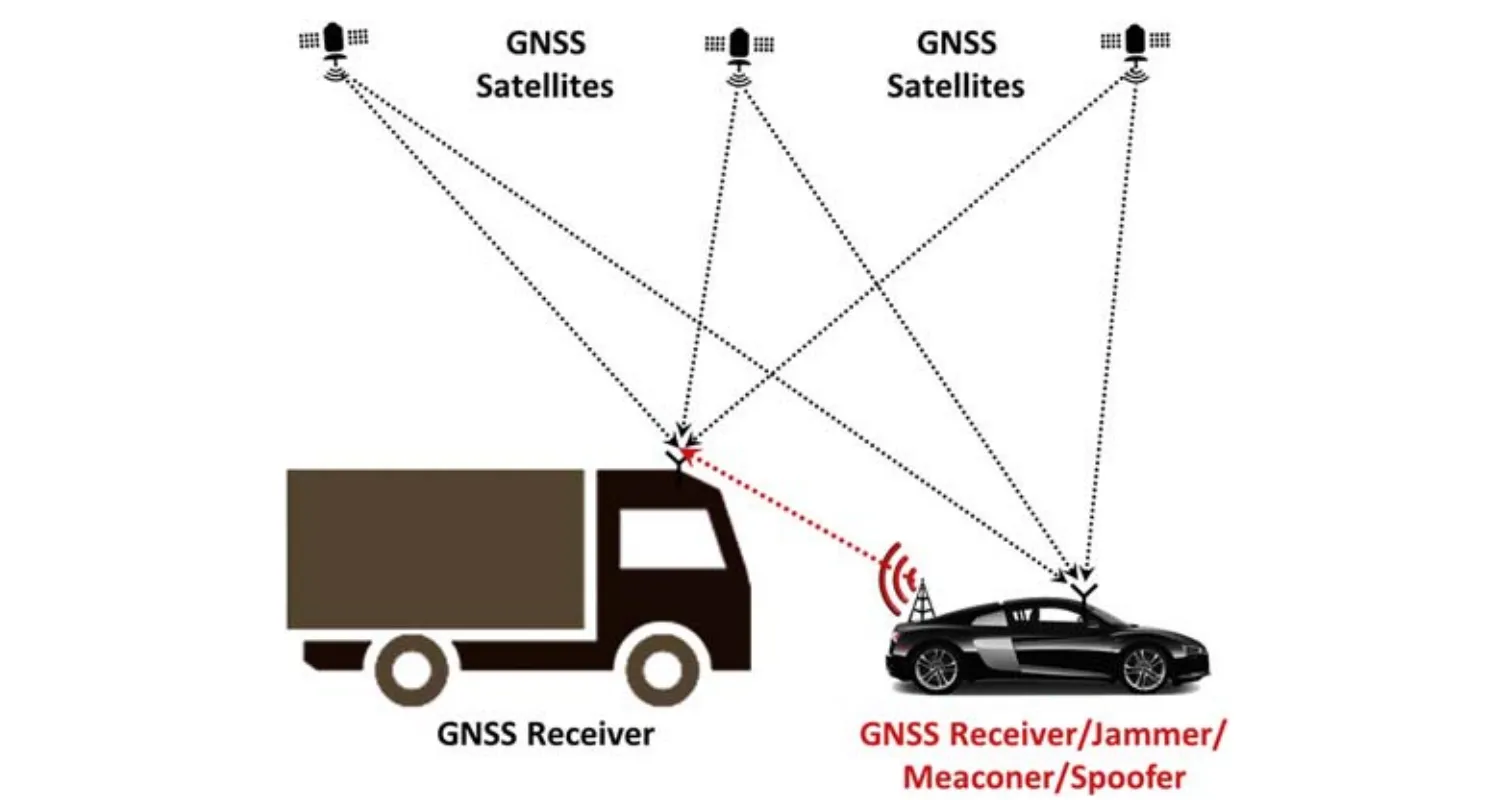
- GNSS jamming: GNSS jammers are devices that intentionally generate harmful interference to GNSS signals to impair or deny their reception. Jammers can be built by people with basic technical competence from readily available commercial components and publicly available information (Fig. 2).
- GNSS meaconing: One of the simplest spoofing techniques is meaconing, i.e., the interception and rebroadcasting of the navigation signals so that the victim computes the ranging information based on the spoofer location and not on the satellites.
- GNSS spoofing: Spoofing is an attack on a GNSS, in an attempt to deceive the GNSS receiver by transmitting powerful false signals that mimic the signals from the true GNSS, exceeding the power of these true signals. Spoofer is a complex computer and radio equipment for the implementation of GNSS spoofing.
3. How to Safeguard Your Products Against GNSS Vulnerabilities?
3.1 Receiver Anti-Spoofing Method
To counteract spoofing, GNSS receivers must discern counterfeit signals amidst a blend of genuine and counterfeit ones. Upon identifying a satellite signal as counterfeit, it can be disregarded in the positioning calculation.
Receiver spoofing protection can vary across different levels, analogous to security measures in a home intrusion detection system. This spectrum ranges from basic entry alarms to more sophisticated movement detection systems. For heightened security, one might opt for additional features like video image recognition, breaking-glass sound detection, or a combination thereof.
Similar to an unprotected house vulnerable to unauthorized access, an unsecured GNSS receiver is susceptible to even rudimentary forms of spoofing. Conversely, fortified receivers employ various methods to detect spoofing, including analyzing signal irregularities or utilizing signals specifically engineered to thwart spoofing attempts, such as Galileo OS-NMA and E6, or the GPS military code.
Jamming and spoofing can be a threat for every business. However, there are several tools in the market that help detect and locate the source of the interference, and you can find receivers with built-in interference mitigation technology. ER-SR-680 GNSS receiver (Fig. 3) integrates advanced anti-jamming technology to achieve highest levels of security.

3.2 Install GNSS Firewall
Another approach is a GNSS firewall that is installed between the GNSS receiver and its antenna. The GNSS firewall analyzes the GNSS signal according to a known set of rules and cuts off false signals.
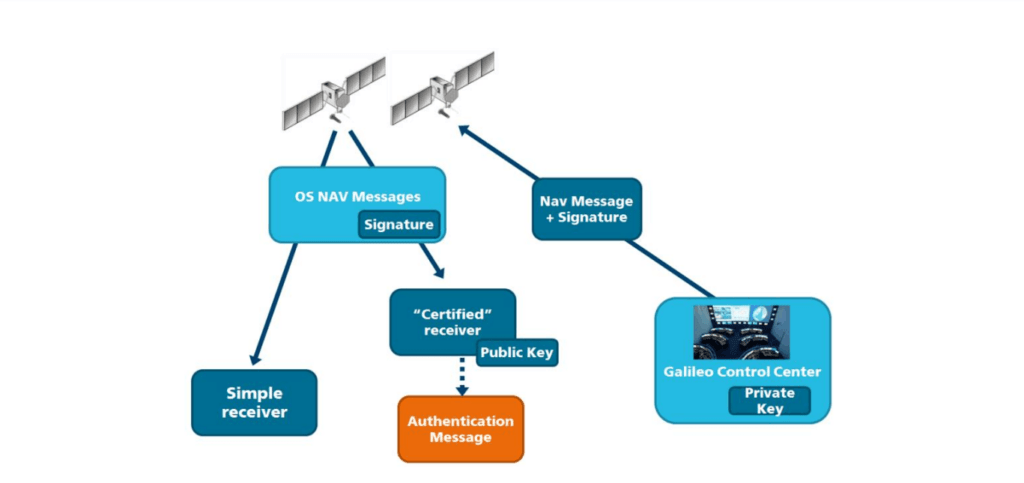
Various countries are investing in ensuring that GNSS is resistant to counterfeiting by creating a security system directly on their satellites. With OS-NMA (Open service NMA), Galileo became the first satellite system to introduce a spoofing protection service directly on a civil GNSS signal.
OS-NMA is a free service on the Galileo E1 frequency. It allows you to authenticate navigation data on Galileo satellites and even on GPS satellites. Such navigation data carry information about the satellite's location and, if changed, will lead to incorrect calculation of the receiver's location.
The Galileo system will offer a commercial E6 authentication service (CAS) with the highest level of security for security-critical applications such as autonomous vehicles. Signal strength encryption will be based on the same methods as military GPS signals. Only receivers that have a secret key can track such encrypted signals. The secret key is also required for generating the signal, which makes it impossible to fake it. Figure 4 shows a brief description of the OS-NMA.
3.3 Antennas Should Be Positioned Correctly
For spoofing attacks, antennas should be positioned so that they are less likely to pick up ground-based signals and to place them where they cannot be seen by the public. Install GNSS antennas in areas where they are not visible to the public or set up barriers such as plastic fencing that would hide their location without interfering with signals.
The obvious approach is based on the use of four-antenna GNSS receivers and beamforming technology. This technology not only filters out noise and interference but also allows you to determine the direction from which the signal came. It is most likely that the spoofer is located on the side or bottom, but it is unlikely coming from the top.
3.4 Multi-Constellation and Multi-Frequency Reception
Leveraging multiple satellite constellations and frequency bands enhances GNSS resilience by increasing signal availability and diversity. By receiving signals from multiple GNSS constellations (Fig. 5), such as GPS, Galileo, and GLONASS, GNSS receivers can mitigate the impact of signal blockage or interference caused by localized jamming or spoofing incidents. Similarly, utilizing multi-frequency reception capabilities enables receivers to distinguish between authentic and spoofed signals more effectively, improving overall system robustness.
3.5 Physical Security Measures
Protecting GNSS infrastructure and equipment from physical tampering and unauthorized access is essential to maintaining system integrity and reliability. Deploying secure enclosures, tamper-evident seals, and access control mechanisms helps prevent unauthorized individuals from tampering with GNSS antennas, receivers, and related hardware components. Additionally, implementing secure installation practices and monitoring systems can detect and deter potential security breaches, ensuring the continuous operation of GNSS systems.
Other advanced anti-spoofing antenna such as ER-MA-02 antenna are available today, read more about this product here.
4. Conclusion.
In conclusion, securing GNSS systems against malicious attacks and vulnerabilities is paramount to preserving their integrity, reliability, and availability. By employing a comprehensive approach mentioned above can enhance GNSS security and mitigate the risks posed by evolving security threats. Implementing the five proven methods outlined in this article will help ensure the continued functionality and trustworthiness of GNSS systems in an increasingly interconnected and technologically reliant world.
I will appreciate it if you find this article help you a lot. For more information, please read the articles and products below.
More Technical Questions
1. Enhance Navigation Accuracy: Advancements in GNSS INS Integration
2. Analysis of Spoofing Detection and Mitigation Techniques for GNSS
3. Construction Surveying: Unleashing New Energy with the Help of GNSS
4. Performance Analysis of GNSS RTK Timing
5. Precision Mapping in Mining Operations: The Role of GNSS Augmentation Technology
6. Intelligent Urban Positioning: Using Multi-GNSS with 3D Mapping
Products in Article







